Lizamoon is an attack on web sites. But if that was the limit of it then it would be a matter of concern only to server administrators. However once the website gets infected it becomes a distribution site for a rather nasty bit of malware for every visitor.
Lizamoon is named after the web site that it was first  noticed on. However once experts knew what to look for, earlier infections were found. In less than four months, there are now over one and a half million web sites that have been infectedwith the Lizamoon virus!
noticed on. However once experts knew what to look for, earlier infections were found. In less than four months, there are now over one and a half million web sites that have been infectedwith the Lizamoon virus!
How Lizamoon infects a web site.
Many web sites do not consist of discreet pages on a server but rather a program called a content management system that stores all the bits and pieces of all the pages in a database and then assembles the bits from the database as any particular page is requested. For example this blog uses a very popular content management system called WordPress. If the content management system is poorly designed or the web server insufficiently secure, a technique called a SQL injection attack can sneak extra bits into the database and thus into all of the pages of the web site.
From the Website to the Visitor, and the con begins
Many security softwares already detect and block the specific Lizamoon software. However, malware creators and copycats are constantly creating new variants. This discussion will necessarily be limited to Lizamoon’s general type of attack. Lizamoon is not the first attack of this type and will certainly not be the last.
With improving security on client computers, much of the effort in malware in recent years has been toward ‘human engineering’. Simply put, this means tricking people. The script that Lizamoon adds to a website is a particularly mean-spirited and cynical scam called a Scareware/Rogue Antivirus Attack. What gets inserted into the website’s page is a tiny bit of script that re-directs to another web site. Such scripts are not unusual so their presence on a page is not an automatic cause for concern to the security software running on the computer.
I was reminded when watching the classic movie The Sting that the Lizamoon virus is really just like the the old fashioned real world con job in the movie: it has the setup, the hook, the story, and the sting. The infection of the website was the setup. When someone visits the site, the con job begins in earnest with the hook: a phony warning message that a virus has been detected and to click some button to protect the computer. That ‘scareware’ is the hook. The message often contains more than one choice, but they all do the same thing. An extra nasty version of the Scareware hook will draw a phony border around the picture so that using the X on the window border also has the same effect. The most complete versions will also trap any keystrokes so that the user can’t use Ctrl-Alt-Delete to kill the process.
With the user frightened into taking the hook, they may also say yes to any operating system generated messages about whether or not to install the software. The site then pretends be installing an antivirus and performing a system scan. The system scan is fake but the installation is real. The software is installing an imitation antivirus to replace your real one. It will also usually install a back door software. At this point your computer is completely vulnerable to the hackers.
But the con job is just starting. Next comes the story. The phony antivirus now tells a tale of how you have infected files! A truly amazing number of infected files! Your computer is simply crawling with all sorts of infected files all over the place! Moreover, to clean all these infections and to prevent further infections you must buy the ‘full version’ of the antivirus software.
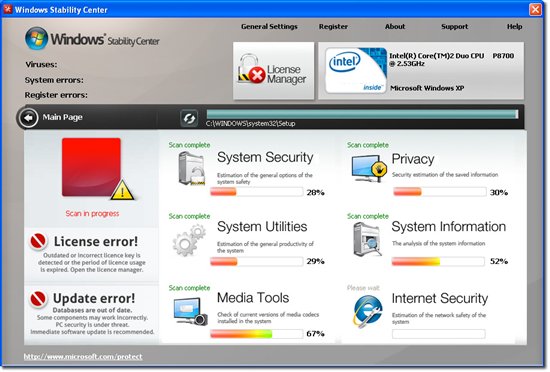
The above is the bogus “Microsoft Stability Center” that is typically displayed at the final stage by Lizamoon. They went to a lot of trouble to make the story look like it was a real protection suite keeping you safe and certainly worth the money to buy the ‘full version’, right? If you agree, you are taken to what looks like a web site in order to purchase the ‘full version’ by giving your personal information and credit card number. Hello identity theft! That’s the sting that the whole con has been building to.
Here’s the ‘sting’ of the Lizamoon con job. It’s really professional looking, with all the right graphics. They are even helpful enough to assist in finding the security code on the card.
The few times I encountered Rouge AV infections on user computers, they often prove difficult to remove. If the Rogue AV writer is crafty, they will remove system restore points and leave one or more stubs that will re-install the software after it has been removed.
The Final Step in Securing Your Computer
Obviously the first step in securing your computer is to have an anti-virus/anti-malware software installed. With Microsoft Security Essentials among others providing free, unobtrusive, and easily updated solutions, there is no excuse not to do so. The second step is to be sure that your computer is configured to automatically download and install critical and security updates as well as virus definition files. Again there is no excuse not to.
However, neither of those will protect you from an attack like this because the goal of the con job is to scare you into replacing your security software with the dummy one. Scareware like Lizamoon has just one chance to frighten you into installing it. If you can recognize that it is not your security software but an invader, you can beat the con job before it goes any further. In short, don’t play the chump. See through the hook and do not take it.
The final step in securing your computer is this: Know the name of your security software and how it normally displays warning messages. Most security software tries to be unobtrusive and does not throw up a window over the top of your work. Typically the messages will rise up from the bottom right corner or in a notification balloon. All of the messages will identify themselves by the name of the software and most will have a distinctive color and graphics. That is done to make it easy to recognize them.
What is the correct action to a scareware warning message? Do not click anywhere on the scareware window at all, particularly if the border, fonts, or colors look in any way different that the ones that your computer normally displays. If the border looks normal, you might try closing it with the X in the upper right hand corner. Otherwise hit Ctrl-Alt-Del on the keyboard, open the task manager, and end the task on your browser. If it turns out that the scareware is blocking the Ctrl-Alt-Del keys from working, then use the power button to turn off the computer. If for any reason the rogue antivirus starts installing or pretending to perform a scan, power off the computer immediately and answer that you want to restore to the last good configuration upon restarting.


1 ping
[…] It is exactly the sort of scareware/Rogue AV attack as has been common for some time and which we recently covered regarding Lizamoon. The only particular difference is the style of the graphics. Since this type of malware is launched […]